A week in security (August 25 – August 31)
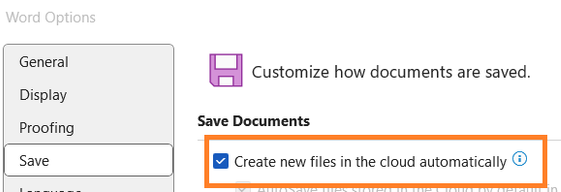
Last week on Malwarebytes Labs: Microsoft wants to automatically save your Word docs to the cloud “No place in our networks”: FCC hangs up on thousands of voice operators in robocall war Claude AI chatbot abused to launch “cybercrime spree” Developer verification: a promised lift for Android security More vulnerable stalkerware victims’ data exposed in […]
A week in security (August 25 – August 31) Leggi tutto »